Project Management
Jun 23, 2025
By
Sammy Jones
Project management is the cornerstone of bringing innovative IT solutions to life. From developing new software applications to implementing robust cybersecurity measures, effective project management ensures projects are delivered on time, within budget, and meet the organization’s specific needs. Let’s learn about the different types of IT Projects.
Have you read our articles on project implementation and implementing a plan?
What are the various categories of IT Projects?
The following table delves into various IT project categories with examples highlighting a specific project, outlining the key tasks involved, and the criteria used to measure its success. Exploring these real-world scenarios will give you a comprehensive understanding of how project management principles translate into practical applications within the IT domain.
The Non-IT Project Implementation Framework provides a solid foundation for managing projects across various industries. However, IT projects introduce complexities that necessitate additional considerations.
This section dives deeper into the specific nuances of IT project implementation, exploring the unique challenges and best practices associated with navigating the ever-evolving world of technology.
Software Development Project Implementation Plan

This plan outlines the key steps for implementing a software development project. Each step includes three crucial actions to ensure a successful outcome.
1. Planning and Requirements Gathering
Define Project Goals and Objectives: Clearly define the software’s purpose, target audience, and desired functionalities. Conduct user interviews and workshops to gather specific needs and expectations.
Develop a Project Scope Statement: Document the project’s boundaries, including functionalities to be developed, those excluded, and any integration requirements with existing systems.
Create a Work Breakdown Structure (WBS): Break down the project into manageable tasks and subtasks, outlining the hierarchy and dependencies between them.
2. Design and Development
Develop System Architecture: Design the overall technical framework of the software, including hardware and software components, databases, and communication protocols.
Choose Development Methodology: Based on project complexity and desired level of flexibility, select an appropriate methodology (e.g., waterfall or agile). For the past ten years, agile methodology has been commonly followed in development projects.
Implement Development Practices: Enforce coding standards, version control systems, and unit testing procedures to ensure code quality and maintainability.
3. Testing and Deployment
Conduct Unit Testing: Developers write and execute tests for individual software components to ensure they function as intended.
Perform Integration Testing: Test how different software modules interact with each other to ensure seamless functionality of the entire system.
Execute User Acceptance Testing (UAT): Involve end-users in testing the software to identify usability issues and ensure it meets their needs.
4. Launch and Maintenance
Develop Deployment Plan: Define the approach for deploying the software to production servers, including rollback procedures in case of unforeseen issues.
Provide User Training and Support: Offer user manuals, training sessions, and ongoing support channels to assist users with adopting the new software effectively.
Monitor System Performance and Security: Continuously monitor the software for bugs, performance issues, and potential security vulnerabilities. Implement a process for addressing these issues promptly.
5. Project Closure and Evaluation
Conduct Project Retrospective: Review the project’s successes and challenges to identify areas for improvement in future endeavors.
Document Lessons Learned: Capture key takeaways and best practices encountered throughout the project lifecycle for future reference.
Archive Project Documentation: Organize and store project documentation (e.g., requirements, design documents, code) for future maintenance and reference.
Software Implementation Project Implementation Plan

This plan outlines a roadmap for successfully implementing a new software solution within an organization. Each step highlights three critical actions for achieving a smooth and effective transition.
1. Preparation and Assessment
Evaluate Current State: Assess existing workflows, data formats, and any legacy systems that need integration with the new software.
Identify Key Stakeholders: Pinpoint individuals or groups impacted by the software implementation, including end-users, IT support staff, and management.
Develop a Communication Plan: Establish clear communication channels for keeping stakeholders informed about the implementation process, timelines, and training opportunities.
2. Configuration and Integration
Configure Software Features: Tailor the software functionalities to match the organization’s specific needs and workflows. This may involve customizing settings, data fields, and user permissions.
Integrate with Existing Systems: Ensure the new software seamlessly interacts with existing databases, applications, and other software used within the organization. Data migration strategies should be addressed at this stage.
Conduct System Testing: Perform thorough testing to identify and resolve any bugs or compatibility issues within the configured software environment.
3. Training and User Adoption
Develop Training Materials: Create comprehensive training materials (e.g., user manuals, video tutorials) that effectively communicate the software’s functionalities and benefits to end-users.
Deliver User Training Sessions: Conduct in-person or online training sessions to equip users with the knowledge and skills necessary to utilize the software effectively.
Provide Ongoing Support: Establish a support structure to address user questions, troubleshoot issues, and offer ongoing guidance as users become familiar with the new software.
4. Go-Live and Post-Implementation
Develop a Go-Live Plan: Outline the process for deploying the software to production, including data migration, user account activation, and communication protocols for launch day.
Monitor System Performance: Continuously monitor the software’s performance after going live to identify performance issues or unexpected behavior.
Gather User Feedback: After going live, actively solicit feedback from users to assess their experience, identify areas for improvement, and refine training materials as needed.
5. Project Closure and Optimization
Document Lessons Learned: Capture key takeaways and best practices encountered throughout the implementation process to inform future software deployments.
Evaluate Project Success: Measure the project’s success against established goals, such as user adoption rates, increased efficiency, or cost savings.
Plan for Ongoing Optimization: Develop strategies for continuous improvement, including exploring new software features, addressing user feedback, and staying updated with future software releases.
Customer Onboarding Project Implementation Plan

This plan outlines a structured approach for implementing a successful customer onboarding program. Each step identifies three crucial actions to ensure a smooth and positive experience for your new customers.
1. Planning and Design
Define Ideal Customer Journey: Map the ideal customer experience from initial signup to becoming a fully engaged user. This includes identifying key touchpoints and milestones.
Develop Onboarding Content: Create informative and engaging content (e.g., tutorials, knowledge base articles, welcome emails) that guides customers through product features and functionalities.
Design User Interface (UI) Onboarding Flows: Develop intuitive UI elements within the product itself that guide users through initial setup and highlight key features.
2. Automation and Personalization
Automate Repetitive Tasks: Utilize automation tools to streamline repetitive tasks like sending welcome emails, provisioning user accounts, and triggering personalized content delivery.
Segment Customer Cohorts: To personalize the onboarding experience, segment your customer base into groups based on user type, needs, or signup behavior.
Leverage Customer Data: Utilize customer data (e.g., signup information and product usage) to personalize onboarding content and recommendations.
3. Training and Support
Develop a Multi-Channel Support System: Offer various support channels (e.g., live chat, email ticketing, knowledge base) to cater to different customer preferences and learning styles.
Train Customer Support Representatives: Equip customer support representatives with in-depth product knowledge and onboarding best practices to assist new customers effectively.
Offer In-Product Guidance: Integrate contextual help resources and tutorials within the product itself to provide immediate assistance during the onboarding process.
4. Feedback and Optimization
Collect Customer Feedback: Actively solicit feedback from customers through surveys, A/B testing, and user interviews to identify areas for improvement.
Analyze User Onboarding Data: Track key metrics like completion rates, time spent on tasks, and support ticket volume to assess the effectiveness of your onboarding program.
Continuously Improve: Based on feedback and data analysis, refine your onboarding content, personalize the experience further, and optimize the overall customer journey.
5. Measurement and Reporting
Define Success Metrics: Establish clear metrics to measure the effectiveness of your onboarding program, such as customer activation rates, time-to-value, and customer satisfaction scores.
Generate Onboarding Reports: Regularly generate reports that track onboarding metrics and identify trends to inform data-driven decisions.
Communicate Onboarding Results: Communicate the success of your onboarding program to stakeholders, highlighting the positive impact on customer retention and engagement.
New IT Infrastructure Project Implementation Plan
Building a robust and scalable IT infrastructure is crucial for any organization. This plan outlines a structured approach for implementing a brand-new IT infrastructure project, highlighting three key actions in each step.
1. Planning and Design
Define Infrastructure Requirements: Conduct a thorough analysis of the organization’s current and future IT needs, considering factors like user base size, data storage demands, and desired application capabilities.
Develop Infrastructure Architecture: Design the blueprint for the new infrastructure, including hardware components (servers, storage devices, network equipment), software (operating systems, virtualization platforms), and network topology.
Select Vendors and Technology Partners: Research and compare different vendors, evaluating factors like product features, scalability, pricing, and vendor reputation before selecting technology partners for hardware, software, and implementation services.
2. Procurement and Deployment
Finalize Procurement Contracts: Negotiate and finalize contracts with vendors for hardware, software licenses, and any necessary implementation or maintenance services.
Equipment Acquisition and Delivery: Secure the necessary hardware components, ensuring timely delivery and proper configuration according to the designed infrastructure architecture.
System Installation and Configuration: This involves physically installing hardware, configuring software applications, and integrating all components within the new IT infrastructure.
3. Testing and Validation
Conduct System Integration Testing: Test the functionality and compatibility of different hardware and software components within the new infrastructure to ensure seamless operation.
Perform Performance Testing: Evaluate the performance of the new infrastructure through load testing and stress testing to ensure it can meet the organization’s performance requirements under various user loads.
Develop a Disaster Recovery Plan: Craft a comprehensive disaster recovery plan that outlines procedures for data backup, system redundancy, and swift recovery in case of unforeseen outages or disruptions.
4. Go-Live and User Transition
Develop User Migration Plan: Plan the process for migrating users and applications from the existing infrastructure to the new one, minimizing downtime and disruption to ongoing operations.
Data Migration and Cutover: Execute the data migration process according to the defined plan, ensuring data integrity and transferring critical information to the new storage systems.
Post-Migration Monitoring and Support: Continuously monitor the performance of the new infrastructure after going live, providing ongoing support to users as they transition to the new environment.
5. Project Closure and Optimization
Document Project Completion: Compile detailed documentation of the new IT infrastructure, including system configurations, network diagrams, and vendor manuals for future reference.
Evaluate Project Success: Measure the project’s success against established goals, considering factors like budget adherence, performance improvements, and user satisfaction with the new infrastructure.
Plan for Ongoing Maintenance and Upgrades: Establish a plan for ongoing maintenance, system updates, and future infrastructure upgrades to ensure the long-term stability, security, and scalability of the new IT environment.
Upgrade IT Infrastructure Project Implementation Plan
Upgrading an existing IT infrastructure requires careful planning to minimize disruption and ensure a smooth transition. This plan outlines a structured approach for implementing an IT infrastructure upgrade, highlighting three key actions in each step.
1. Assessment and Planning
Evaluate Current Infrastructure: Conduct a comprehensive assessment of the existing infrastructure, identifying performance bottlenecks, capacity limitations, and any outdated hardware or software components.
Define Upgrade Goals and Objectives: Clearly define the desired outcomes of the upgrade project, such as improved performance, increased storage capacity, or enhanced security capabilities.
Develop Upgrade Strategy: Develop a detailed upgrade strategy outlining the specific components targeted for upgrade, the upgrade sequence, and any potential migration efforts required for data or applications.
2. Resource Allocation and Procurement
Identify Resource Requirements: Determine the resources needed for the upgrade, including personnel with relevant technical expertise, additional hardware or software licenses, and any necessary temporary resources.
Secure Budget Approval: Obtain necessary budget approval based on the estimated costs for hardware, software, potential downtime expenses, and any required training for staff.
Procure Upgrade Components: Procure the necessary hardware and software components according to the defined upgrade strategy, ensuring timely delivery and compatibility with the existing infrastructure.
3. Staging and Testing
Develop a Staging Environment: Set up a separate staging environment to test the upgraded components and configurations before deploying them to the production environment. This minimizes risk and allows for troubleshooting in a controlled setting.
Perform Upgrade Testing: Conduct rigorous testing within the staging environment to validate the functionality, compatibility, and performance of the upgraded infrastructure. This includes testing system integration and user applications.
Develop Rollback Plan: Establish a comprehensive rollback plan that outlines procedures for reverting to the previous infrastructure configuration if unforeseen issues arise during the upgrade process.
4. Deployment and User Transition
Execute Upgrade Plan: Deploy the upgrade according to the defined upgrade strategy, minimizing downtime and ensuring a smooth transition between the old and new infrastructure configurations.
Data Migration and User Training: If necessary, migrate data to new storage systems and train users on the upgraded hardware or software functionalities to minimize disruption and ensure user adoption.
Post-Upgrade Monitoring and Support: Continuously monitor the performance of the upgraded infrastructure after deployment, providing ongoing support to users as they adjust to the new environment.
5. Project Closure and Optimization
Document Upgrade Process: Document the entire upgrade process, including configurations, migration procedures, and lessons learned for future reference and knowledge sharing within the IT team.
Evaluate Upgrade Success: Measure the project’s success against established goals, assessing performance improvements, capacity expansion achieved, and user satisfaction with the upgraded infrastructure.
Plan for Ongoing Maintenance: Develop a plan for ongoing maintenance of the upgraded infrastructure, including system updates, security patches, and monitoring for future capacity needs or technological advancements.
Business Process Automation Implementation Plan
This plan outlines a roadmap for successfully implementing business process automation (BPA) within your organization. Each step highlights three crucial actions to ensure a smooth and efficient transition.
1. Identify and Analyze Processes
Map Current Processes: Visually document existing business processes, including key steps, decision points, and stakeholders involved. Utilize tools like flowcharts or process mapping software.
Identify Automation Opportunities: Analyze mapped processes to pinpoint repetitive, manual tasks or workflows that can be effectively automated through technology.
Prioritize Automation Projects: Prioritize automation projects based on factors like potential cost savings, improved efficiency, and impact on employee productivity. Focus on high-volume, error-prone tasks for maximum benefit.
2. Select and Implement Automation Tools
Evaluate BPA Tools: Research and compare different Business Process Automation (BPA) tools based on features, integration capabilities, scalability, and budget considerations.
Develop Implementation Plan: Create a detailed implementation plan for your chosen BPA tool, outlining training requirements, data migration strategies, and testing procedures.
Configure and Integrate Tools: Configure the BPA tool to automate identified processes, integrate it with existing systems for seamless data flow, and ensure data security protocols are followed.
3. User Training and Change Management
Develop Training Materials: Create comprehensive training materials (e.g., video tutorials and user manuals) to equip employees with the knowledge and skills to utilize the new automated processes effectively.
Conduct User Training Sessions: Provide in-person or online training sessions to guide users through the new workflows and address any concerns or questions related to automation.
Communicate and Promote Change: Effectively communicate the benefits of BPA to employees, address potential anxieties about job security, and encourage user adoption of the new automated processes.
4. Testing and Deployment
Perform System Testing: Thoroughly test the automated workflows within the BPA tool to identify and address any bugs or functionality issues before deployment.
Develop Rollout Strategy: Establish a rollout strategy for deploying the automated processes, considering factors like user impact and potential disruption to ongoing operations.
Pilot Launch and Monitor Performance: First, pilot launch the automation in a controlled environment, then monitor its performance to identify areas for improvement before full deployment.
5. Measurement and Continuous Improvement
Define Success Metrics: Establish clear metrics to measure the effectiveness of your BPA initiatives, such as processing time reduction, error rate decrease, and employee productivity gains.
Track and Analyze Data: Track key metrics throughout the automation process, analyzing data to identify areas for further optimization and potential additional automation opportunities.
Refine and Update Processes: Continuously refine and update automated processes based on user feedback, data analysis, and evolving business needs to ensure long-term effectiveness.
Cybersecurity Project Implementation Plan

This plan outlines a structured approach for implementing a successful cybersecurity project. Each step identifies three crucial actions to enhance your organization’s security posture.
1. Risk Assessment and Planning
Identify Critical Assets: Catalog your organization’s critical assets, including data, hardware, software, and intellectual property. Prioritize based on their sensitivity and potential impact if compromised.
Conduct Threat Assessment: Evaluate potential cyber threats your organization faces, considering factors like industry trends, common attack vectors, and the evolving threat landscape.
Develop a Cybersecurity Strategy: Craft a comprehensive cybersecurity strategy that aligns with your organization’s risk tolerance and outlines key initiatives to mitigate identified threats and protect critical assets.
2. Implement Security Controls
Strengthen Network Security: Implement network security measures, such as firewalls, intrusion detection/prevention systems (IDS/IPS), and access control lists (ACLs), to monitor and control network traffic.
Enforce Endpoint Security: To prevent malware infections, deploy endpoint security solutions such as antivirus, anti-malware, and application control software on all devices accessing your network.
Implement Data Security: Implement data encryption methods at rest and in transit and establish data access controls to restrict access to sensitive information based on the principle of least privilege.
3. User Awareness and Training
Develop Security Awareness Programs: Develop and deliver ongoing security awareness training programs to educate employees on cybersecurity best practices, including password hygiene, phishing email identification, and social engineering tactics.
Simulate Phishing Attacks: Conduct regular phishing simulations to test user awareness and identify areas where employees might be susceptible to social engineering attacks.
Promote a Culture of Security: Foster a culture of security within your organization by encouraging employees to report suspicious activity and emphasizing the importance of cybersecurity for business continuity.
4. Incident Response and Recovery
Develop an Incident Response Plan: Craft a detailed incident response plan outlining procedures for detecting, responding to, and recovering from security incidents to minimize damage and downtime.
Test and Refine the Plan: Regularly test your incident response plan through simulations to ensure its effectiveness and refine procedures based on identified weaknesses.
Maintain Backups and Disaster Recovery: Maintain secure and up-to-date backups of critical data and systems to facilitate swift recovery in case of a cyberattack or other disaster.
5. Monitoring and Continuous Improvement
Implement Security Information and Event Management (SIEM): Utilize SIEM solutions to aggregate and analyze security logs from various sources, enabling centralized monitoring for potential threats and suspicious activity.
Conduct Regular Vulnerability Assessments: Regularly conduct vulnerability assessments to identify weaknesses in your security posture and prioritize patching known security vulnerabilities in software and systems.
Stay Informed and Adapt: Continuously monitor the evolving threat landscape, stay informed about new cyber threats and vulnerabilities, and adapt your security controls and strategies to stay ahead of emerging threats.
Adapting the Project Implementation Framework to Specific IT Project Types

The core project implementation framework provides a solid foundation for managing various IT projects. However, specific IT project types often necessitate additional considerations during the planning and execution phases to ensure successful delivery. Here’s a table summarizing how the framework can be adapted to cater to distinct IT project categories:
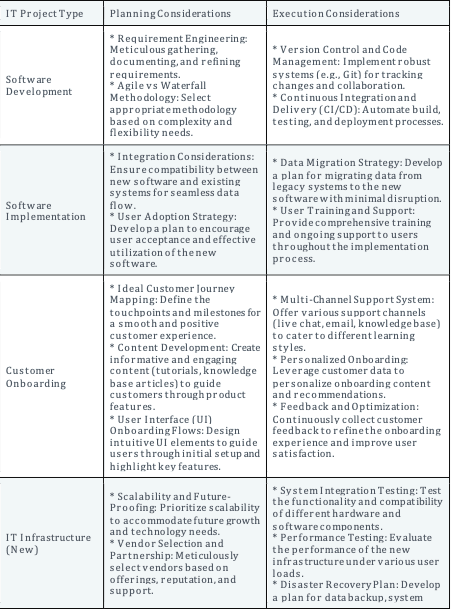
By adapting the core framework to incorporate these project-specific considerations during the planning and execution phases, IT project managers can significantly increase the chances of successful project delivery and achieve their desired outcomes within the ever-evolving IT landscape.
Summarization and Conclusion
The provided IT Project Implementation Framework offers a robust roadmap for guiding tech projects. This guide has provided a comprehensive framework for implementing various IT projects. It outlines critical actions within each crucial phase: Planning and Assessment, Configuration and Integration, Training and User Adoption, Go-Live and Post-Implementation, and Project Closure and Optimization.
We’ve further explored how to adapt this framework to address the specific needs of different IT project types. From software development and infrastructure upgrades to customer onboarding and cybersecurity initiatives, each project category requires unique planning and execution considerations. By incorporating these project-specific adjustments, IT project managers can significantly enhance their chances of successful delivery and maximize the value achieved from their IT investments.
In conclusion, a well-defined implementation plan coupled with a tailored approach for distinct project types empowers IT teams to navigate the complexities of IT projects and achieve successful outcomes.
Check this blog for a deeper dive into non-IT project management methodologies.
Frequently Asked Questions
What are the different stages of the IT Project Implementation Framework?
The IT Project Implementation Framework outlines five crucial phases:
Planning and Assessment: This stage involves defining project goals, identifying stakeholders, and developing a communication plan.
Configuration and Integration (for Software Implementation): This stage focuses on configuring software functionalities, integrating with existing systems, and conducting system testing.
Go-Live and Post-Implementation: This stage includes deploying the project (software, infrastructure, etc.), monitoring system performance, gathering user feedback, and planning for ongoing optimization.
Project Closure and Optimization: This stage involves documenting lessons learned, evaluating project success, and planning for future maintenance and upgrades.
How does this framework adapt to different IT project types?
The core framework remains the same, but additional considerations are needed during planning and execution for specific project types. Here are some examples:
Software Development: Requires meticulous requirement gathering, version control systems, and CI/CD practices.
Software Implementation: Focuses on Integration with existing systems, user adoption strategies, and data migration plans.
Customer Onboarding: Emphasizes mapping the ideal customer journey, creating engaging content, and personalizing the onboarding experience.
New IT Infrastructure: Prioritizes scalability, vendor selection, and disaster recovery planning.
IT Infrastructure Upgrade: Requires an upgrade strategy, resource allocation, and a rollback plan in case of issues.
Business Process Automation: Focuses on selecting high-impact processes for automation, ensuring compatibility with existing systems, and managing change within the organization.
Cybersecurity involves considering compliance requirements, gathering threat intelligence, and regularly testing incident response procedures.
What are the benefits of using this framework?
By adapting the core framework to specific project types, IT project managers can significantly increase their chances of successful project delivery and achieve desired outcomes within the ever-evolving IT landscape.
You may also like
A Guide to Project Management Professional Certification
Jun 18, 2025
Laugh Your Way to Productivity: 50 Workplace Quotes
Jun 18, 2025
50 Funny Workplace Memes That’ll Brighten Your Workday.
Jun 18, 2025
What Does a Customer-First Mindset Mean? Explained in 2025
Nov 3, 2025
What It Takes to be a Great Customer Success Manager in 2025
Aug 11, 2025
Resolve Common Customer Complaints into Powerful Experiences
Nov 4, 2025








